Overthewire Natas Level 8 -> Level 9
Solution for the Overthewire.org Natas level 8 -> Level 9
Description
Username: natas9
URL: natas9.natas.labs.overthewire.org
Solution
Visit the url http://natas9.natas.labs.overthewire.org in the browser and we get a prompt for login.
Use the username natas9 and the password obtained from the previous challenge.
Once logged in we can see a text box and a search button
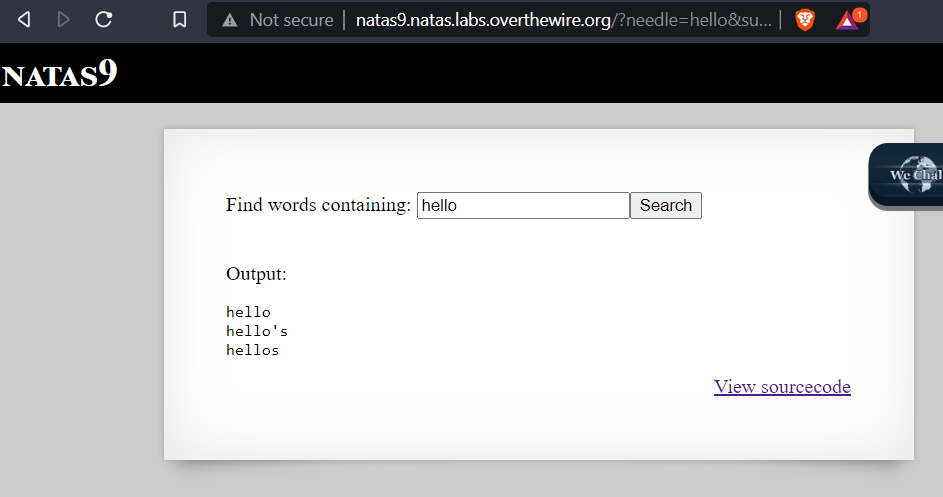
When entering text into the box and clicking search button the app appears to search a file for the text we entered.
Checking the View sourcecode link will show php code used for the search button.
1
2
3
4
5
6
7
8
9
10
11
<?
$key = "";
if(array_key_exists("needle", $_REQUEST)) {
$key = $_REQUEST["needle"];
}
if($key != "") {
passthru("grep -i $key dictionary.txt");
}
?>
The php code takes our input and uses passthru to execute a command.
The command is using grep to search a file for the text we entered.
Because the php script is not sanitizing our input before passing it to grep we can use command injection to insert our own command and have it be executed.
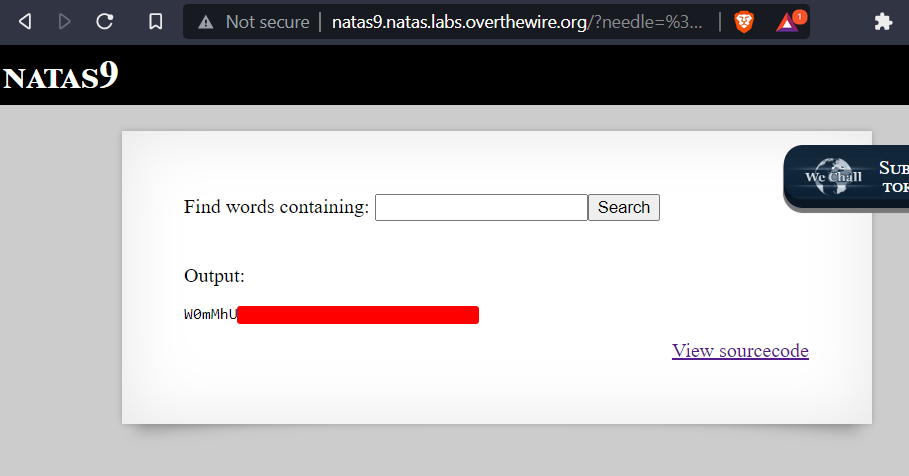
First we end the grep command by using a ; and then we can type our own command like cat to read the password file. The # is to comment out everything after our command otherwise the entire contents of dictionary.txt would also be printed to the screen.
1
;cat /etc/natas_webpass/natas9 #
Entering the command into the search box and clicking on search will give the password.